What is Octelium?
Octelium is a free and open source, self-hosted, unified zero trust secure access platform that is flexible enough to operate as a modern zero-config remote access VPN, a comprehensive Zero Trust Network Access (ZTNA)/BeyondCorp platform, an ngrok/Cloudflare Tunnel alternative, an API gateway, an AI/LLM gateway, a scalable infrastructure for access and deployment to build MCP gateways and A2A architectures/meshes, a PaaS-like platform, a Kubernetes gateway/ingress alternative and even as a homelab infrastructure.
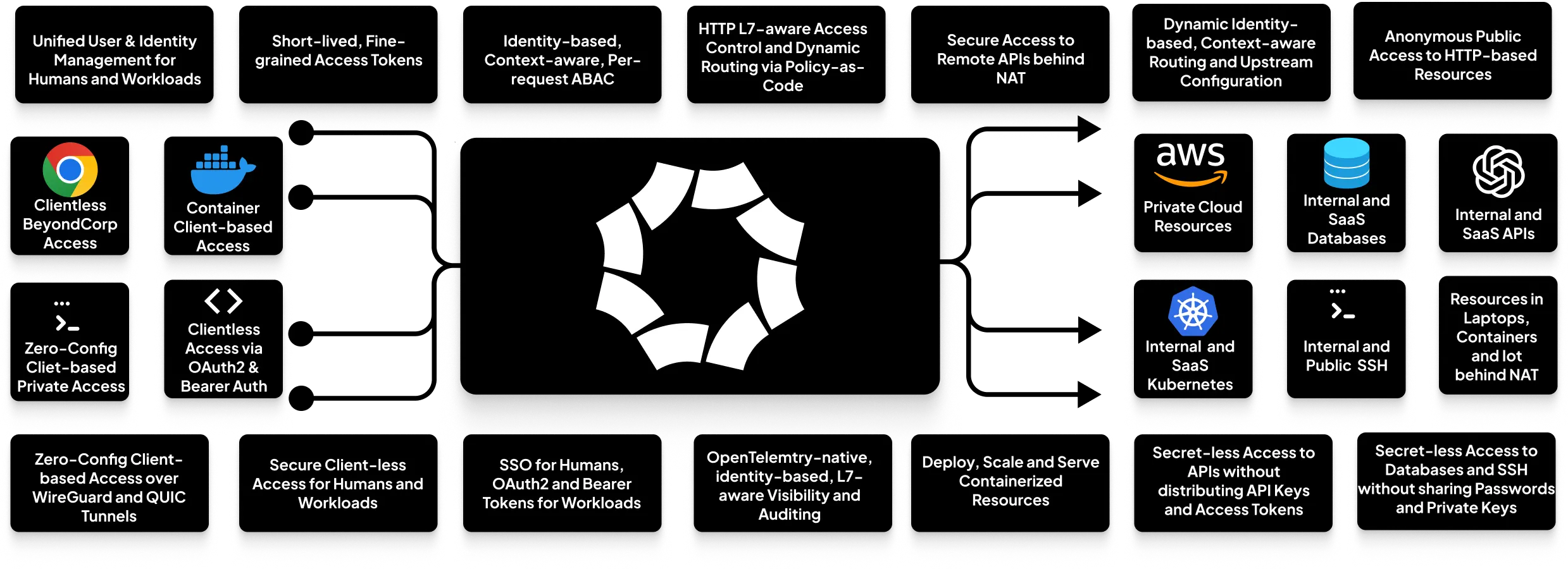
Octelium provides a scalable zero trust architecture (ZTA) for identity-based, application-layer (L7) aware secretless secure access via both private client-based access over WireGuard/QUIC tunnels as well as public clientless access, for both humans and workloads, to any private/internal resource behind NAT in any environment as well as to publicly protected resources such as SaaS APIs and databases, via context-aware access control on a per-request basis.
Use Cases
Octelium is a versatile platform that can serve as a complete or partial solution for many different needs. Here are some of the key use cases:
- Modern Remote Access VPN: A zero-trust, layer-7 aware alternative to commercial remote access/corporate VPNs like OpenVPN Access Server, Twingate, and Tailscale, providing both zero-config client access over WireGuard/QUIC and clientless access via dynamic, identity-based, context-aware Policies.
- Unified ZTNA/BeyondCorp Architecture: A comprehensive Zero Trust Network Access (ZTNA) platform, similar to Cloudflare Access, Google BeyondCorp, or Teleport.
- Self-Hosted Secure Tunnels: A programmable infrastructure for secure tunnels and reverse proxies for both secure identity-based as well as anonymous clientless access, offering a powerful, self-hosted alternative to ngrok or Cloudflare Tunnel. You can see an example here.
- Self-Hosted PaaS: A scalable platform to deploy, manage, and host your containerized applications, similar to Vercel or Netlify. See an example for Next.js/Vite apps.
- API Gateway: A self-hosted, scalable, and secure API gateway for microservices, providing a robust alternative to Kong Gateway or Apigee. You can see an example here.
- AI Gateway: A scalable AI gateway with identity-based access control, routing, and visibility for any AI LLM provider. See an example here.
- Unified Zero Trust Access to SaaS APIs: Provides secretless access to SaaS APIs for both teams and workloads, eliminating the need to manage and distribute long-lived and over-privileged API keys. See a generic example here, AWS Lambda here, and AWS S3 here.
- MCP Gateways and A2A-based Architectures A secure infrastructure for Model Context Protocol (MCP) gateways and Agent2Agent Protocol (A2A)-based architectures that provides identity management, authentication over standard OAuth2 client credentials and bearer authentication, secure remote access and deployment as well as identity-based, L7-aware access control via policy-as-code and visibility (see an example here).
- Homelab: A unified self-hosted Homelab infrastructure to connect and provide secure remote access to all your resources behind NAT from anywhere (e.g. all your devices including your laptop, IoT, cloud providers, Raspberry Pis, routers, etc...) as well as a secure deployment platform to deploy and privately as well as publicly host your websites, blogs, APIs or to remotely test heavy containers (e.g. LLM runtimes such as Ollama, databases such as ClickHouse and Elasticsearch, Pi-hole, etc...). See examples for remote VSCode, and Pi-hole.
- Kubernetes Ingress Alternative: A more advanced alternative to standard Kubernetes ingress controllers and load balancers, allowing you to route to any Kubernetes service via dynamic, L7-aware policy-as-code.
Main Features
-
A modern, unified, scalable zero trust architecture Octelium is built from the ground up to control access at the application layer using a scalable architecture that is based on identity-aware proxies (IAPs) rather than at the network level using segmentation as is the case in remote access VPNs with the following main goals:
- A unified access platform for humans and workloads.
- A unified architecture to access any kind of private/internal resources behind NAT (e.g. on-prem, one or more private clouds, your own laptop behind NAT, IoT, etc...) as well as protected public resources (e.g. SaaS APIs, databases, protected public SSH servers, etc...).
- A unified architecture for both zero trust access methods:
- Private access using VPN-like zero-config client-based zero trust network access (ZTNA) over WireGuard/QUIC tunnels with automatic private DNS.
- Public clientless BeyondCorp access for both humans via their browsers and workloads via standard OAuth2 client credential flows and bearer authentication.
- Built on top of Kubernetes to provide automatic horizontal scalability and availability. An Octelium Cluster can run on top of a single node Kubernetes cluster running over a cheap cloud VM instance/VPS and it can also run over managed, scalable Kubernetes installations.
-
Dynamic secretless access Octelium's layer-7 awareness enables Users to seamlessly access resources that are protected by application-layer credentials eliminating the need to expose, manage and share such typically long-lived and over-privileged secrets required to access such protected resources. The following protocols are currently supported:
- HTTP-based resources (e.g. HTTP APIs, gRPC APIs, protected web apps, etc...) without having to share and expose API keys, access tokens or OAuth2 client credentials.
- SSH without having to share passwords or manage keys and certificates.
- Kubernetes clusters without sharing Kubeconfigs, certificates or access tokens.
- PostgreSQL and MySQL-based databases without exposing passwords.
- Any application-layer protocol that is protected by mutual TLS (mTLS) without managing PKI/sharing certificates.
-
Context-aware, identity-based, application-layer aware access control Octelium provides you a modern, centralized, scalable, fine-grained, dynamic, context-aware, layer-7 aware, attribute-based access control system (ABAC) on a per-request basis using modular and composable Policies that enable you to write your policy-as-code using CEL as well as OPA (Open Policy Agent).
Octelium intentionally has no notion whatsoever of an "admin" or "superuser" User. In other words, zero standing privileges are the default state. Any permissions including those to the API Server can be restricted via Policies and tied to time and context on a per-request basis.
-
Context-aware, identity-based, L7 aware dynamic configuration and routing Route to different upstreams, different credentials representing different upstream contexts and accounts using policy-as-code with CEL and OPA on a per-request basis.
-
Continuous strong authentication A unified, continuous authentication system for both human and workload Users:
- Any web identity provider (IdP) that supports OpenID Connect or SAML 2.0 (e.g. Okta, Auth0, OneLogin, AWS Cognito, etc...) as well as Github OAuth2.
- "Secretless" authentication for workloads via OIDC-based assertions where workloads can authenticate themselves using OIDC identity tokens issued by the identity provider hosting the workload ( e.g. Azure, CI/CD providers such as GitHub Actions as well as Kubernetes clusters, etc...)
- Native support for dynamic MFA/re-authentication/login via FIDO2/WebAuthn/Passkey, TOTP and TPM 2.0.
- Integrate Your IdP and control access to sensitive resources based on NIST SP 800-63 Authenticator Assurance Levels to force using strong MFA (e.g. WebAuthn/Passkeys) via phishing resistant security keys (e.g. Yubikey).
-
OpenTelemetry-ready, application-layer aware auditing and visibility Identity and application-layer aware visibility where every request is logged and exported in real-time to your OpenTelemetry OTLP receivers and collectors which can be further exported to log management and SIEM tools and providers.
-
Effortless, passwordless, serverless SSH access Octelium clients are capable of serving SSH even when they are not running as root enabling Users to SSH into containers, IoT devices or other hosts that do not have or cannot run SSH servers.
-
Effortlessly deploy, scale and secure access to your containerized applications as Services Octelium provides you out-of-the-box PaaS-like capabilities to effortlessly deploy, manage and scale your containerized applications and serve them as Services to provide seamless secure client-based private access, clientless public BeyondCorp access as well as public anonymous access.
-
Centralized, declarative and programmable management Octelium Clusters are designed to be administered like Kubernetes. It can be administered via declarative management where one command (i.e.
octeliumctl apply) is enough to (re)produce the state of the Octelium Cluster anywhere. The Cluster's management is also centralized via its APIs which means you do not have to ever again SSH into your servers to set up configurations/rules. Instead, theocteliumctlCLI tool is used to control all the Cluster's resources in a clean, centralized and declarative way that is dev/DevOps/GitOps-friendly where you can store your Cluster configurations and resources in a git repo and effortlessly reproduce them at anytime and anywhere. Furthermore, the Cluster is fully programmable using gRPC-based APIs that can be compiled to your favorite programming language. -
No change in your infrastructure is needed Your upstream resources don't need to be aware of Octelium at all. They can be listening to any behind-NAT private network, even to localhost. No public gateways, no need to open ports behind firewalls to serve your resources wherever they are.
-
Avoiding traditional VPN networking problems altogether Octelium's client-based private networking mode eliminates a whole class of networking and routing problems that traditional VPNs suffer from. In Octelium, each resource is represented by a Service that is implemented by an identity-aware proxy (IaP) and is assigned stable private dual-stack IP address(es) within a single dual-stack private range abstracting the actual upstream resource's dynamic network details. This architecture eliminates classes of decades-old networking problems via:
- Using a single stable route instead of injecting countless routes of the actual different remote private networks into the users' machines, causing routing conflicts.
- Effortless dual-stack private networking where Users seamlessly access Services via both IPv4/IPv6 regardless of whether the upstream supports them both or not, without having to deal with the pain and inconsistency of NAT64/DNS64.
- A unified, automatically managed, private DNS using your own domain for all resources scattered across the different remote networks that works consistently and independently of the dynamic network details of the upstreams.
- Simultaneous support for WireGuard (Kernel, TUN as well as unprivileged implementations via gVisor) as well as experimentally QUIC (both TUN and unprivileged via gVisor) tunnels via a lightweight zero-config client that can run in any Linux, MacOS, Windows environment as well as container environments (e.g. Kubernetes sidecar containers for your workloads).
-
Open source and designed for self-hosting Octelium is fully open source and it is designed for single-tenant self-hosting. There is no proprietary cloud-based control-plane, nor this is some crippled demo open source version of a separate fully functional SaaS paid service. You can host it on top of a single-node Kubernetes cluster running on a cheap cloud VM/VPS and you can also host it on scalable production cloud-based or on-prem multi-node Kubernetes installations with no vendor lock-in.